“Top 5 ways hackers can bypass your firewall” - Security Boulevard
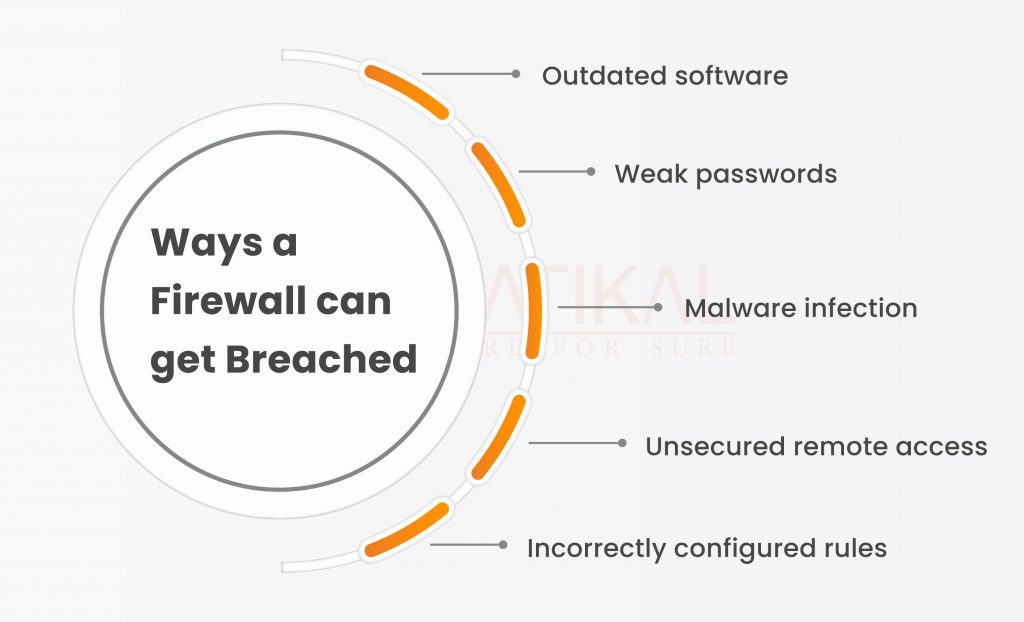
Every firewall in the market is vulnerable to hacking, despite what certain security providers may assert.
One key aspect of cybersecurity is the use of a firewall, which acts as a barrier between your network and the outside world. However, even the most advanced firewall can be breached if not properly configured or maintained.
Google Home speakers were vulnerable to eavesdropping hackers

No matter which great smart speaker you pick for your home, the premise is always the same: You need to trust the company behind it with your voice recordings and other peripheral sounds of your home. But whenever computers are involved, vulnerabilities exist and can be exploited.
Security researcher Matt Kunze noticed that setting up a Google Home speaker with a Google account was pretty easy, all while bringing a ton of powerful tools to the account owner (via Bleeping Computer ).
North Korean hackers are posing as VC firms to steal crypto - and a blockchain expert says 2023 ...
North Korea's infamous Lazarus Group is mimicking venture capital firms and banks to steal cryptocurrencies, according to Kaspersky.
The state-sponsored cybercrime group is creating domains that present themselves as well-known Japanese, US and Vietnamese companies.
Ministers and thousands of civil servants 'are vulnerable to hackers' | Daily Mail Online

Ministers and large numbers of civil servants have been warned they are vulnerable to hackers after personal data was left online.
Experts have voiced alarm that ministers could be easily tricked into revealing sensitive information using a database of contact details.
What is ethical hacking?

White hat hackers are ethical security hackers who test the security of different types of networks, software, and hardware. Those individuals use IT knowledge and hacking skills to identify cybersecurity vulnerabilities without taking personal advantage of them.
White hat hackers respect hacking principles and are considered the good guys who would allow vendors to patch vulnerabilities before they share knowledge about security problems with others.
Hackers may have accessed some patient info at Kelberman Center | Daily Sentinel

The Kelberman Center has issued a warning about a data breach at their facility in early November that may have compromised client information.
Kelberman officials said an unknown party had used a client’s electronic mailbox to gain access to a limited number of user mailboxes for a short period of time between Oct. 31 and Nov. 3.
Hackers Use Excel Add-Ins as Initial Penetration Vector
Although Excel warns about the potential dangers of XLLs, these warnings are usually overlooked by users.
According to experts, hackers combine add-ons written in C++ with add-ons developed using the free tool Excel-DNA. And if the first such experiments of hackers were noticed a few years ago, then in 2021-2022 such attacks began to develop much more actively.
How to tell if your cell phone has been secretly hijacked - WVII / Fox Bangor
WATERVILLE — A community is in shock after a racial slur was left on the walls of one …
RICHMOND — Friday at approximately 9:25 p.m., Maine State Police Troopers responded to a two-vehicle crash that occurred …
A Concert Like No Other
Hop aboard a shuttle to Kepler-1649c. Be there to welcome new lifeforms into the universe. All passengers must have a verified event ticket. There are 10,000 tickets in circulation so no need to panic. Limited seating available per trip. There will be multiple flights each hour shipping off from the NORAD Space Port in Iceland.
Event tickets are non refundable & non transferable (except on the black market. Call Sal with questions.) An event ticket can be reused for up to 9900 yearly transactions.
No sandals allowed on flight. Adults only. Kittens must show a custodian's ID at the gate. You are not allowed to get married while aboard the shuttle. Please arrive early if you are wearing jeans.
NB: EVENT TICKETS CONTAIN A PRIVATE ANONYMOUS DIGITAL IMPRINT.
Reserve your spot. Click here.



Comments
Post a Comment